Operating System Structures
Operating-System Services
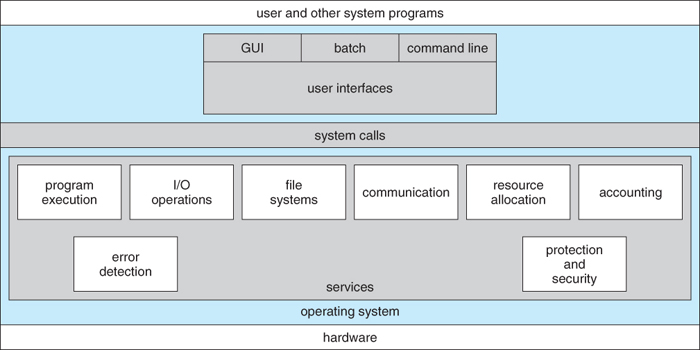
- User Interface
- Command-Line Interface (CLI): which uses text commands and a method for entering them
- Batch interface: commands and directives to control those commands are entered into files, and those files are executed.
- Graphical user interface: a interface using a window system with a pointing device to direct I/O (mouse), choose from menus, make selections and enter text via keyboard
- Program Execution
- The system must be able to load a program into memory and to run that program. The program must be able to end its execution, either normally or abnormally (indicating error).
- I/O Operations
- The OS is responsible for transferring data to and from I/O devices, including keyboards, terminals, printers, and storage devices.
- File-system Manipulation
- a means for programs to read and write files and directories, create and delete directories, search for files, list file information. Permission management to allow or deny access to files or directories
- Communication
- occur between processes that are executing on the same computer or between processes of clustered systems. Implemented via shared memory or through message passing, in which packets of information are moved between processes
- Error detection
- Both hardware and software errors must be detected and handled appropriately, with a minimum of harmful repercussions. Some systems may include complex error avoidance or recovery systems, including backups, RAID drives, and other redundant systems. Debugging and diagnostic tools aid users and administrators in tracing down the cause of problems.
Another set of operating-system services that are not used for helping the user but rather to maintain efficiency of the system.
- Resource Allocation
- E.g. CPU cycles, main memory, storage space, and peripheral devices. Some resources are managed with generic systems and others with very carefully designed and specially tuned systems, customized for a particular resource and operating environment.
- Accounting
- Keeping track of system activity and resource usage, either for billing purposes or for statistical record keeping that can be used to optimize future performance.
- Protection and security
- Preventing harm to the system and to resources, either through wayward internal processes or malicious outsiders.
User Operating-System Interface
Command Interpreter
- Gets and processes user requests and opens requested programs
- in some systems the CI is incorporated directly into the kernel
- more commonly the CI is a separate program that launches once the user logs in or otherwise accesses the systems
Graphical User Interface, GUI
- icons represent some item on the system, and respond accordingly when the icon is activated
- first developed in the early 1970's at Xerox
- in some systems teh GUI is just a front end for activating a traditional command line interpreter running in the background
System Calls
- System calls provide a means for user or application programs to call upon the services of the OS
- Written in C or C++, or Assembly for optimal performance
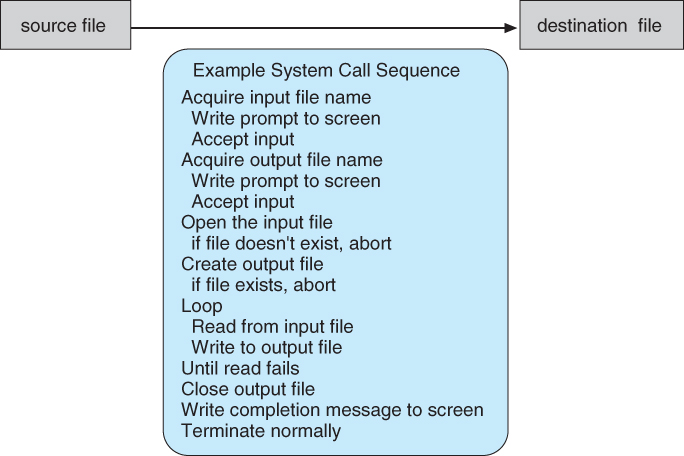
Here is a system call to copy a file:
Most programmers do not use the low-level system calls directly, but instead use an "Application Programming Interface", API. The use of APIs instead of direct system calls provides for greater program portability between different systems. The API then makes the appropriate system calls through the system call interface, using a table lookup to access specific numbered system calls, as shown in below:

Parameters are generally passed to system calls via registers, or less commonly, by values pushed onto the stack. Large blocks of data are generally accessed indirectly, through a memory address passed in a register or on the stack.
Types of System Calls
System calls can be grouped into six major categories, and most of these system calls support or are supported by concepts and functions discussed in later chapters.
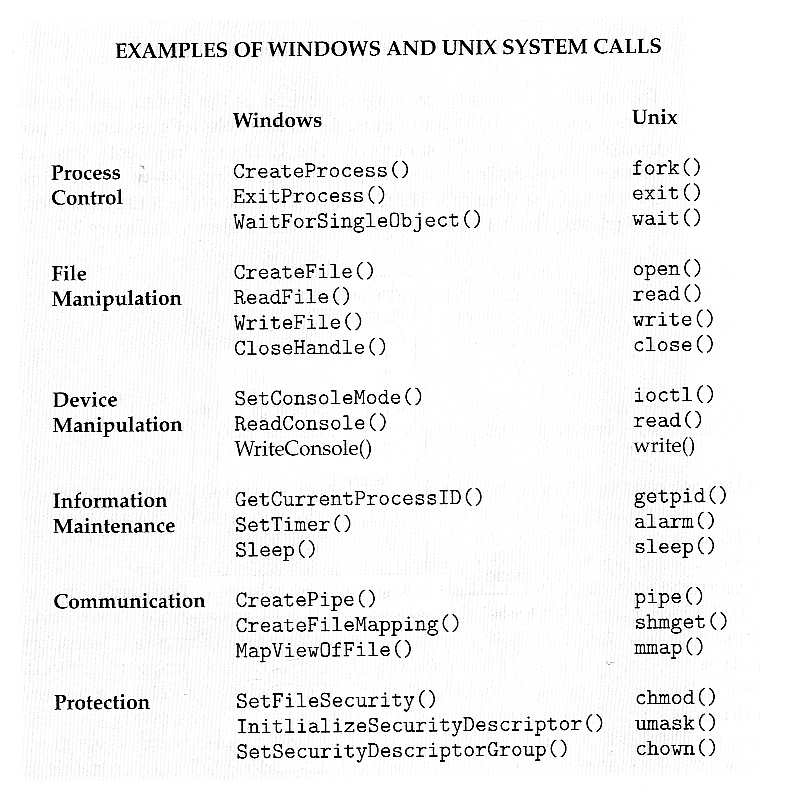
Here are five system calls:

and some more functions:
Process Control
- Process control system calls include end, abort, load, execute, create process, terminate process, get/set process attributes, wait for time or event, signal event, and allocate and free memory.
- Processes must be created, launched, monitored, paused, resumed,and eventually stopped.
- When one process pauses or stops, then another must be launched or resumed
- When processes stop abnormally it may be necessary to provide core dumps and/or other diagnostic or recovery tools.
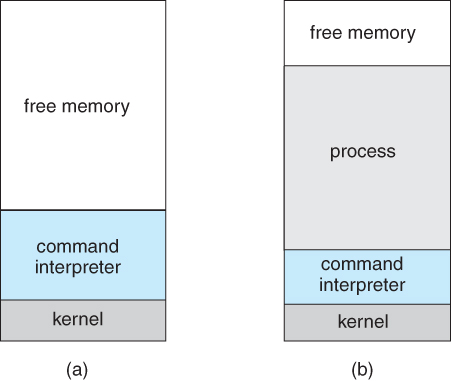
- Compare DOS ( a single-tasking system ) with UNIX ( a multi-tasking system ).
- When a process is launched in DOS, the command interpreter first unloads as much of itself as it can to free up memory, then loads the process and transfers control to it. The interpreter does not resume until the process has completed, as shown below:
File Management
- File management system calls include create file, delete file, open, close, read, write, reposition, get file attributes, and set file attributes.
- These operations may also be supported for directories as well as ordinary files.
Device Management
- Device management system calls include request device, release device, read, write, reposition, get/set device attributes, and logically attach or detach devices.
- Devices may be physical ( e.g. disk drives ), or virtual / abstract ( e.g. files, partitions, and RAM disks ).
- Some systems represent devices as special files in the file system, so that accessing the "file" calls upon the appropriate device drivers in the OS. See for example the /dev directory on any UNIX system.
Information Maintenance
- Information maintenance system calls include calls to get/set the time, date, system data, and process, file, or device attributes.
- Systems may also provide the ability to dump memory at any time, single step programs pausing execution after each instruction, and tracing the operation of programs, all of which can help to debug programs.
Communication
- Communication system calls create/delete communication connection, send/receive messages, transfer status information, and attach/detach remote devices.
- The message passing model must support calls to:
- Identify a remote process and/or host with which to communicate.
- Establish a connection between the two processes.
- Open and close the connection as needed.
- Transmit messages along the connection.
- Wait for incoming messages, in either a blocking or non-blocking state.
- Delete the connection when no longer needed.
- The shared memory model must support calls to:
- Create and access memory that is shared amongst processes ( and threads. )
- Provide locking mechanisms restricting simultaneous access.
- Free up shared memory and/or dynamically allocate it as needed.
- Message passing is simpler and easier, ( particularly for inter-computer communications ), and is generally appropriate for small amounts of data.
- Shared memory is faster, and is generally the better approach where large amounts of data are to be shared, ( particularly when most processes are reading the data rather than writing it, or at least when only one or a small number of processes need to change any given data item. )
Protection
- Protection provides mechanisms for controlling which users / processes have access to which system resources.
- System calls allow the access mechanisms to be adjusted as needed, and for non-privileged users to be granted elevated access permissions under carefully controlled temporary circumstances.
- Once only of concern on multi-user systems, protection is now important on all systems, in the age of ubiquitous network connectivity.